How to create a kill-switched VPN on Mac OS X with Little Snitch
In this post, I describe why, after years of using the wonderful Mac/iOS VPN product, Cloak, I’m experimenting with an alternative approach, that combines Private Internet Access (PIA) and Little Snitch. (2015-08-28 — As mentioned in an update at the end of the article, I've actually now switched back to Cloak, but using Little Snitch as the kill-switch.)
An introduction to Cloak
For years, I’ve used Cloak on both Mac OS X and iOS to provide security when accessing untrusted wifi and ethernet networks.
Technically, Cloak provides this by establishing a VPN (virtual private network) connection to one of their servers, and then routing all your device’s internet traffic through that encrypted tunnel, thereby making it difficult for local sniffers to compromise your computer. Normally, Cloak will connect to whichever of their global servers is fastest, given your current location. But you can also manually specify the server, which can be useful if you’re in Europe, and need to appear to be connected, say, from somewhere within the United States.
Cloak is, without a doubt, the easiest-to-use VPN app on the Mac OS X and iOS platforms. The essential problem that it has solved is — you don’t have to remember to enable it. It does this by maintaining a list of your “trusted networks”, and automatically establishing a secure VPN connection anytime you’re not connected to one of those networks. While other VPN apps attempt to do the same, they are clumsy and unreliable, and as far as I know, there are none that achieve reliable auto-connection on iOS. So with Cloak, once you’ve installed and configured it, you can forget about it, knowing your devices will remain secure wherever you are.
And the elegant visual design of Cloak is representative of the quality you’ll find in all aspects of the product—from its performance, to the account management at the Cloak website, to their prompt, friendly and competent technical support.

For casual needs, the $2.99/5GB monthly plan from Cloak, providing security to all your devices, is a no-brainer and something I’d recommend to everyone.
Motivations for trying something different
Having said that, there are a couple of drawbacks to Cloak that have prompted me to experiment with an alternative.
- At my office, we recently switched from ADSL internet connectivity, to WiMAX. As our computers are now essentially connected to somebody else’s wifi network, I want my MacBook Air to be permanently VPN connected at all times while at work. The only Cloak plan that can provide enough data transfer for that is the $9.99 unlimited plan—and $120/year is just expensive enough to make me consider alternatives. (It's worth noting, though, that Cloak do offer a $100, if you buy a year's service in advance.)
- An important feature of Cloak is called “OverCloak”, which prevents any internet traffic during those few moments between the time when you connect to a network and the time at which the Cloak VPN connection has been established. Commonly known as a “kill-switch”, this feature has the unfortunate side effect that, when enabled, kills access to local network services — e.g. killing the ability of my local-network CrashPlan server from connecting to the Mac at work to perform its backup.
- Finally, there’s the issue of privacy. Cloak (the company) log enough information on their servers to identify your internet activity, and they keep those logs for 16 days. Based on what I do on the internet, this has never been a concern of mine. But as I grow older and gain experience, I’ve found myself more and more interested in privacy, and there are VPN providers out there who do not log any information that can associate you with your internet activity.
Private Internet Access (PIA)
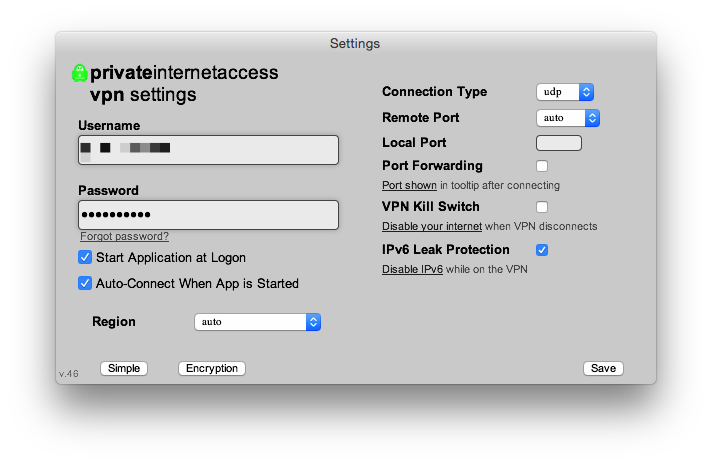
After extensively researching VPN providers, and speaking with some contacts who work in the business of privacy, I concluded that Private Internet Access (PIA) is perhaps the best of today’s VPN providers. They’ve been around a long time, are one of the largest, have servers all over the world, and claim to have a zero logging policy. And for $40/year, their unlimited data plan is three times more economical than Cloak’s.
On the Mac, I set PIA's connection region to “auto”, which attempts to connect to the fastest available VPN server, which, in my case, is usually in France or Germany. As with Cloak, I can also manually set it to connect to a server in the United States, when I need to do banking or whatnot.
As you can see from this screenshot, though, visual design is not PIA’s strong suit:
Using Little Snitch to create a kill switch
PIA provides a kill-switch feature, but just like Cloak, enabling it will affect local-network services. I’ve discovered a solution, however, achieving the same functionality without affecting local-network services, through the use of Little Snitch—a Mac OS X application-level packet filter—and it’s support for automatic profile switching.
In Little Snitch, I have three filtering “profiles”:
- Public (Kill-Traffic)
This is the default profile that is selected whenever my Mac connects to an unknown network, or a network that I’ve manually assigned to it. Since I want to be VPN-connected at all times, you can see from this screenshot that I’ve assigned my home wifi and ethernet networks, my office wifi network, and several wifi networks of other places I’ve visited.
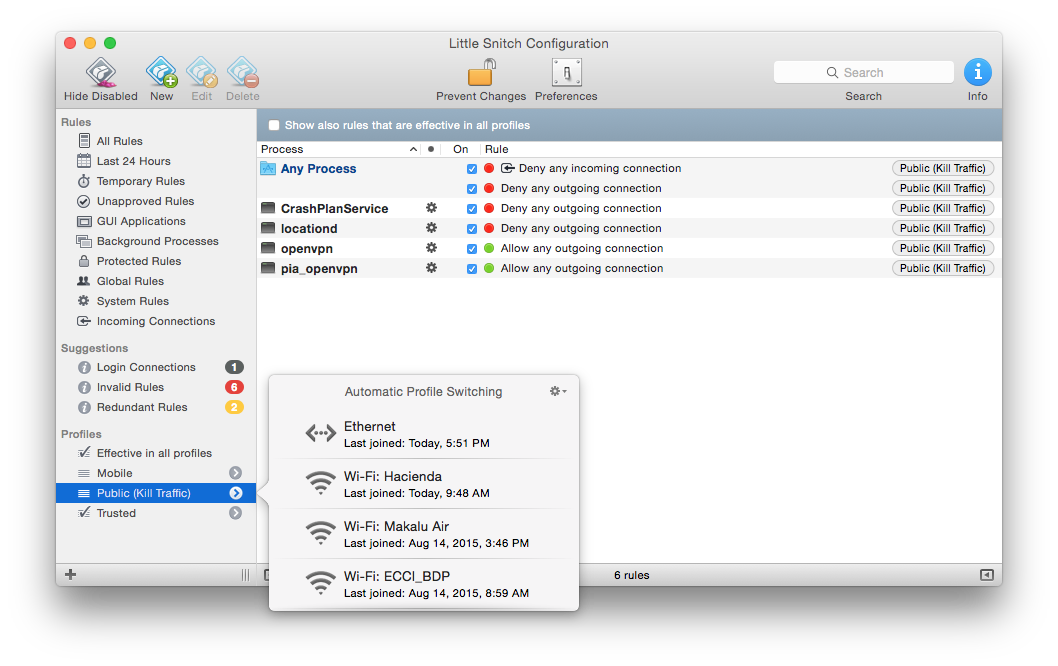
You can also see the rules-set associated with this profile—in which incoming and outgoing connections from any user-process are denied.
Very important, though, you’ll also notice that the “openvpn” and “pia_openvpn” processes are allowed, as these are the processes that apps like PIA and Cloak use to establish their VPN connections.
So, in summary, whenever my Mac is not connected to a VPN (with the exeption of mobile tethering as described below), my “Public (Kill Traffic)” Little Snitch profile is automatically selected, preventing all incoming and outgoing connections.
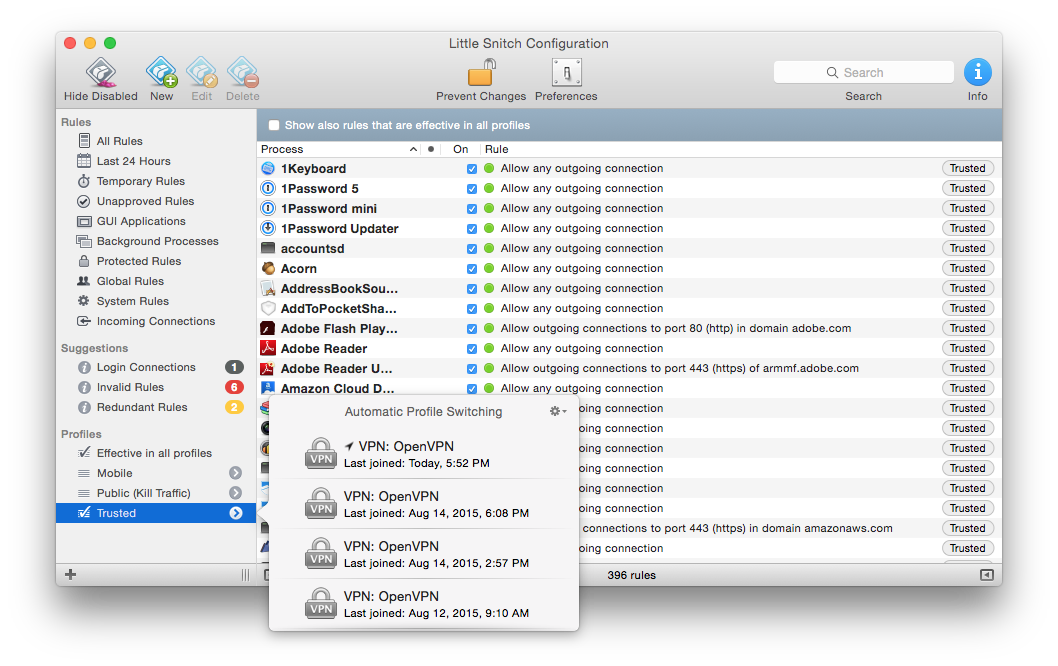
- Trusted
When a VPN connection is established, the Mac sees this as a new “network” called “OpenVPN”, which can therefore be used to trigger a “Trusted” profile in Little Snitch, once again allowing all my desired incoming and outgoing traffic.
- Mobile
I have one other Little Snitch profile, unrelated to VPN connectivity, called “Mobile”. This profile is activated whenever my Mac is connected to my iPhone’s or iPad’s “Personal Hotspot”. The purpose of this profile is to minimize my iOS device’s data usage. As you can see from the screenshot, this profile kills traffic from apps like Dropbox and BitTorrent Sync.

Putting it all together
For $40 per year, this setup provides my Mac with continual and unlimited VPN connectivity, with a reliable provider that does not log any user-session data. It provides kill-switch functionality that prevents any network activity between the time my Mac connects to a network and the time when the PIA VPN connection is established. It’s not nearly as elegant as the Cloak solution, but so far, it’s been working great.
What about iOS? The PIA approach to securing your iOS device is either through their own iOS app, or via the popular (open-source) OpenVPN app. The big downside to both—and a show-stopper in my opinion—is that you still have to remember to activate them. So for iOS, I continue using Cloak and their $2.99/month plan that provides 5GB of data (which more or less matches the amount of monthly data that my wireless carrier provides.)
Will I stick with this setup in the long-run? Time will tell. There are certainly more moving parts involved. So if, with time, my preference for convenience begins to dominate my interests in cost and privacy, or if my view of the risks associated with Cloak’s minimal vs PIA’s zero logging change, it could certainly happen that I switch back to using Cloak exclusively, with their unlimited plan. But in the meantime, it’s great that a workable alternative exists.
2015-08-28 Update — Back to Cloak
After an enjoyable conversation with Dave Peck of Cloak, I've now switched from PIA back to Cloak as the VPN component of my setup. Cloak have since modified their logging policy to something I'm comfortable with. They're also going to investigate an advanced preference to allow local network access override of OverCloak on untrusted networks, but given the Little Snitch method of providing kill-switch functionality (described above), that's now less of an issue for me.
I really like Cloak—both the product and the people behind the product, and am happy to be able to continue to support them.
Enjoy this article? — You can find similar content via the category and tag links below.
Categories — Technology, Products
Questions or comments? — Feel free to email me using the contact form below, or reach out on Twitter.
